Introduction
As digital transformation accelerates across industries and everyday life, the cybersecurity landscape is being reshaped at an unprecedented pace. In recent years, cyber threats have grown not only in volume but also in sophistication, with attackers increasingly leveraging automation, machine learning, and generative technologies. As a result, traditional security models are no longer sufficient on their own. Instead, artificial intelligence has emerged as a critical force in modern cybersecurity, enabling faster detection, smarter prevention, and more adaptive responses to evolving risks.
In 2026, AI-driven cybersecurity innovations are being widely adopted by enterprises, small businesses, and individual users alike. From real-time threat detection and predictive intelligence to deepfake mitigation and identity protection, AI is being used to strengthen defenses across digital environments. Moreover, these technologies are not only improving security outcomes but are also reducing response times, minimizing human error, and enhancing overall resilience against complex cyberattacks.
1. Autonomous Threat Detection & Response Systems

Traditional cybersecurity systems rely heavily on static rules and signatures, which struggle to keep pace with dynamic threats. Today’s AI-driven systems ingest massive volumes of telemetry and network data, learning baseline behaviors and instantly recognizing anomalies.
These systems are capable of analyzing millions of network events per second, allowing near-instant detection of malware, lateral movement, and other suspicious activities across digital environments. Once a threat has been identified, automated response engines are triggered to isolate affected devices, block malicious traffic, and initiate remediation workflows, often without requiring human intervention.
This innovation is especially impactful for small organizations and individual users who lack large security teams, as AI can fill the gap with predictive protections and automated reactions.
2. Predictive Threat Intelligence
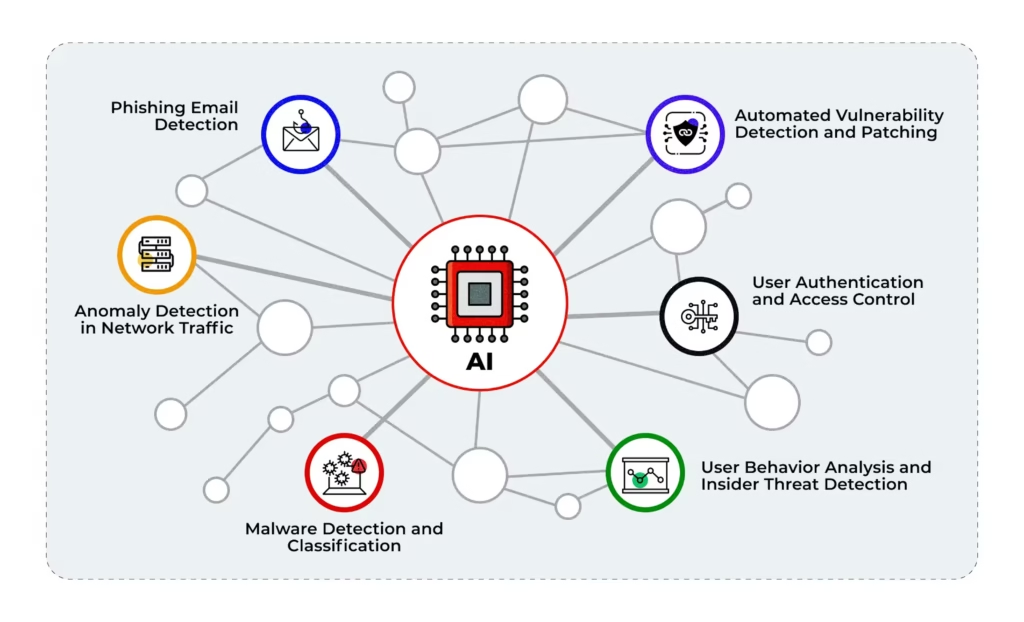
Rather than reacting to breaches after they happen, AI now drives predictive threat intelligence — analyzing historical attack patterns, global threat feeds, and contextual risk signals to forecast upcoming threats.
Predictive AI models are designed to prioritize the most likely risk vectors and vulnerabilities, enabling proactive defense planning before attacks occur. Through this approach, cybersecurity is transformed from a reactive practice into a preventative strategy, significantly reducing the potential impact of breaches through early detection, timely mitigation, and strategic patching.
For consumers, this means fewer phishing emails reaching inboxes. For businesses, this translates to fewer costly intrusions and better allocation of security resources.
3. AI-Enhanced Zero Trust & Identity Management

Zero Trust Architecture (ZTA) has become a cornerstone of modern cybersecurity. Rather than assuming internal network trust, every user and device must continuously prove legitimacy.
AI enhances Zero Trust systems by contextualizing access decisions using continuous analysis of user behavior, device posture, geographic location, and real-time risk indicators. When access anomalies are detected—such as simultaneous logins from different countries or unusual activity patterns—AI models automatically trigger adaptive authentication measures or impose access restrictions to prevent unauthorized entry.
This layered approach helps protect sensitive data and systems even if credentials are compromised — a frequent target in today’s threat landscape.
4. Deepfake & Synthetic Media Detection

Deepfake technology — AI-generated audio, video, and images — has empowered threat actors to create convincing impersonations for fraud, phishing, and misinformation campaigns.
Dedicated platforms such as Vastav AI are specifically designed to detect manipulated media across multiple formats, helping both consumers and enterprises avoid costly deception and identity-based fraud. By leveraging advanced machine learning techniques, AI models can analyze inconsistencies in facial movements, voice patterns, and pixel-level artifacts, allowing fake or synthetically generated content to be accurately identified and flagged.
With the rise of remote work and virtual meetings, this technology is crucial for authenticating communications and preventing identity-based fraud.
5. Next-Gen Endpoint Detection & Response (EDR)

Endpoints — laptops, mobile devices, IoT gadgets — remain a prime target for breaches. AI-driven Endpoint Detection & Response tools can continuously monitor behavior and quickly contain threats.
Leading solutions such as Darktrace and CrowdStrike Falcon exemplify how AI is being applied to modern endpoint security. Darktrace is known for its self-learning AI that continuously adapts to normal network behavior and is capable of stopping threats preemptively, while CrowdStrike Falcon combines machine learning with cloud-based threat intelligence to protect devices globally through real-time detection and response.
These AI models reduce false positives and provide actionable insights for both users and business security teams.
6. AI in Phishing & Email Protection

Phishing remains one of the most common and damaging cyber threats. Modern phishing campaigns leverage AI to tailor messages, making them harder to distinguish from legitimate emails.
AI models powered by natural language processing (NLP) are capable of identifying subtle lexical and contextual anomalies that reveal phishing attempts, even when messages closely resemble legitimate communications. Once suspicious content is detected, these systems can automatically flag, quarantine, or rewrite malicious messages, thereby protecting users while maintaining uninterrupted and efficient communication workflows.
For individuals, this means fewer scam emails. For organizations, it significantly increases the resilience of corporate email systems.
7. Security Orchestration, Automation, and Response (SOAR) with AI
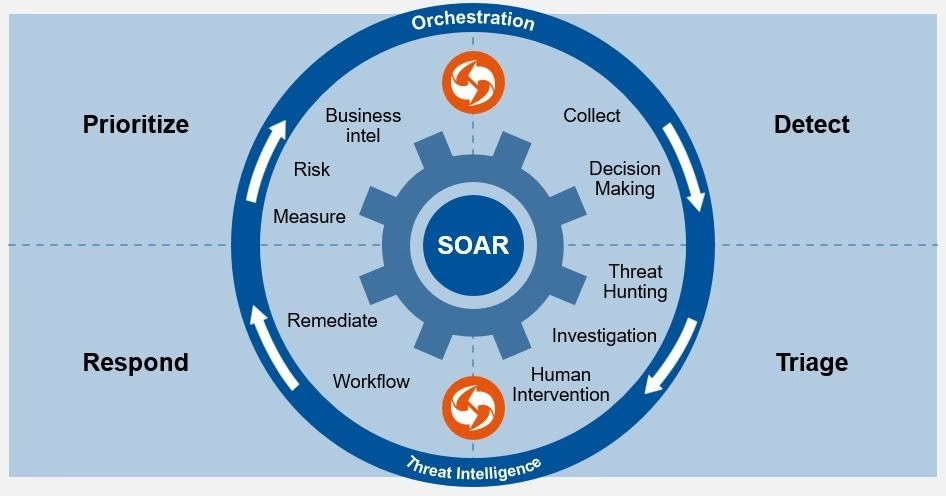
AI-driven SOAR platforms help unify detection, investigation, and response across disparate tools and datasets.
AI can be used to automate incident response playbooks by executing actions such as quarantining affected systems, rolling out security policy changes, and updating firewall rules without the need for manual coordination. As a result, response times are significantly improved, decisions are made more intelligently, and security analysts are freed to focus on higher-level investigations and strategic threat analysis.
SOAR solutions are particularly valuable in enterprise environments where multiple tools and policies must be synchronized rapidly.
8. Explainable & Lightweight AI for Edge Security

Not all AI systems run in the cloud. Recent research highlights frameworks built for near-real-time threat detection on edge devices with interpretability and efficiency in mind.
Explainable AI frameworks assist security professionals in understanding why a model has flagged a potential threat, enhancing trust in automated systems and enabling more accurate and informed responses. At the same time, edge-optimized AI models deliver robust protection for smart devices by operating efficiently without heavy computational requirements or reliance on deep cloud infrastructure, ensuring real-time security across distributed environments.
This innovation is critical as consumer gadgets and industrial IoT systems proliferate.
9. AI-Powered Vulnerability Discovery
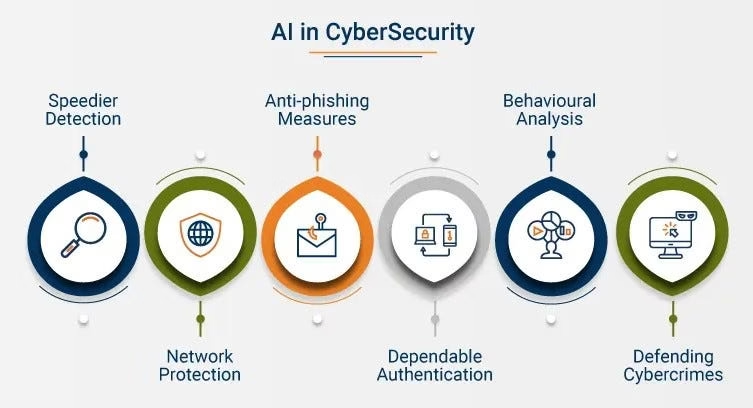
AI isn’t just defensive; it’s now being used to discover security vulnerabilities that traditional tools miss.
In early 2026, Anthropic’s Claude Opus 4.6 model demonstrated breakthrough capabilities by identifying over 500 previously unknown high-severity vulnerabilities in open-source libraries — an accomplishment that advances enterprise vulnerability management significantly.
These AI-driven assessments help developers and security professionals patch software proactively and keep threats at bay.
10. AI Governance & Secure AI Development Tools
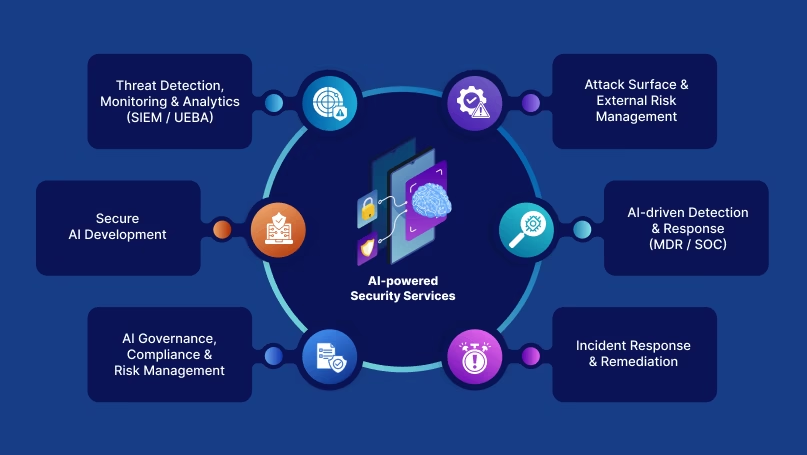
As AI becomes embedded in security tools, companies are also investing in AI governance and security management platforms, addressing risks such as model manipulation, data bias, and unchecked autonomous actions.
A major development in the market is Varonis’ acquisition of an AI security governance company, a strategic move aimed at expanding its capabilities in oversight, risk management, and the secure deployment of AI-driven cybersecurity solutions.
This underscores the growing importance of securing the security systems themselves, particularly as they become more autonomous and critical.
Conclusion
Artificial intelligence isn’t just a buzzword in cybersecurity — it’s the engine driving the next generation of defense capabilities. From autonomous threat detection to deepfake mitigation and AI governance tools, innovations in 2025-2026 are making cyberspace safer for everyone.
However, AI isn’t a silver bullet. Human expertise, robust policy frameworks, and continuous monitoring remain essential complements to AI systems. By combining machine speed with strategic oversight, organizations and individuals can stay resilient in a rapidly evolving threat landscape.
For those seeking to strengthen their digital defenses, understanding, adopting, and responsibly managing AI-driven cybersecurity innovations will be crucial in the years ahead.
Keep up with the latest TECH trends – click here
![]()



